Introducing Avocado Reveal-AI: The Future of Application Security
Avocado Systems has redefined enterprise application security with Avocado Reveal-AI, the next evolution of our groundbreaking runtime threat modeling platform. Powered by advanced AI, Reveal-AI doesn’t just identify vulnerabilities — it guides you through mitigation in real time, bringing security expertise directly into your development workflow. Learn more
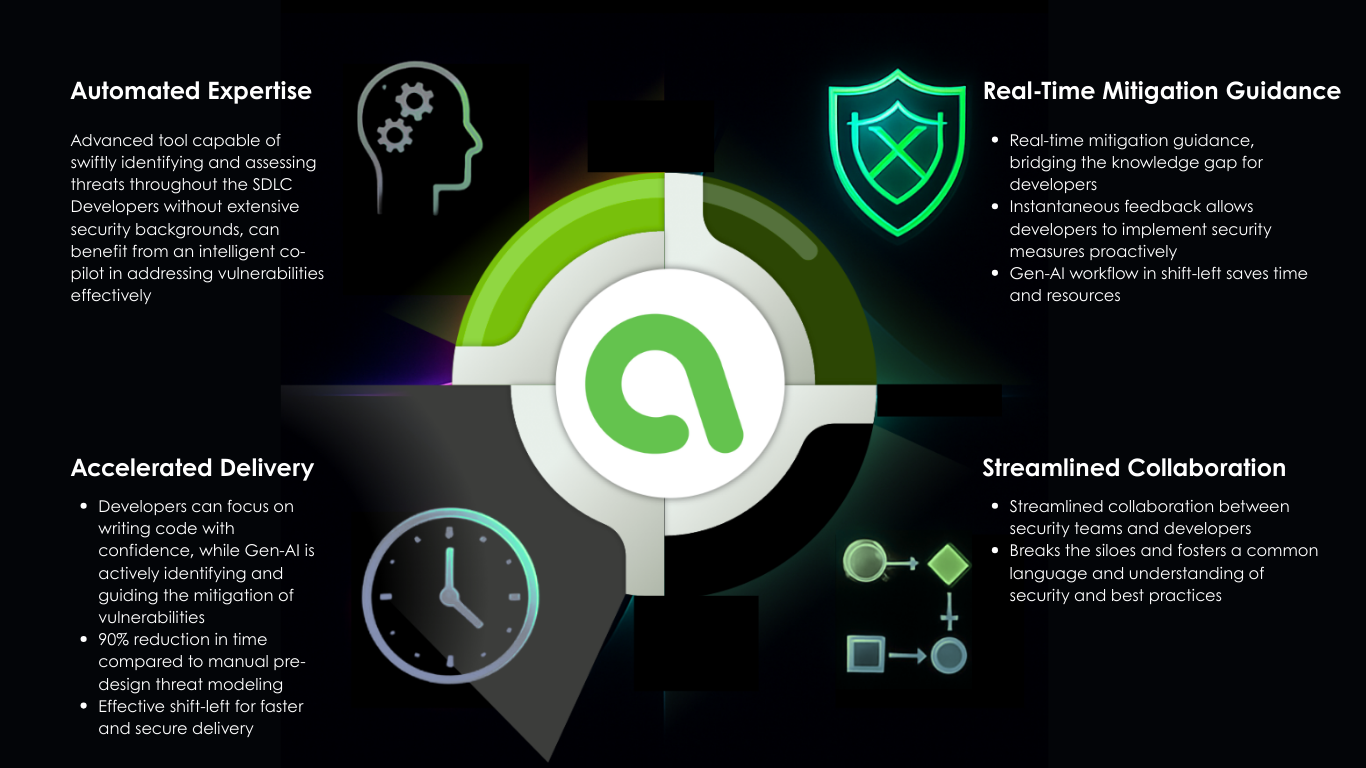
Go beyond simple scanning with AI-driven Runtime Application Threat Modeling that automatically creates intelligent threat models, adapting them to your application’s dynamic runtime behavior. Immediately act on security issues using Real-Time Mitigation Guidance, which delivers actionable, step-by-step recommendations to fix vulnerabilities faster, eliminating the delays of manual reviews.
The platform ensures Streamlined Collaboration by providing built-in tools that allow security and development teams to work together seamlessly, reducing friction and accelerating the secure software development lifecycle. This comprehensive system ultimately leads to Accelerated Application Delivery, enabling your enterprise to ship secure applications faster than ever with confidence against evolving threats.
Key Value Propositions
- AI-Driven Threat Modeling
Go beyond detection. Reveal-AI delivers automated, intelligent threat models that adapt to your application’s runtime behavior. - Real-Time Mitigation Guidance
Get actionable insights and step-by-step recommendations to fix vulnerabilities faster—without waiting for manual reviews. - Streamlined Collaboration
Security and development teams work together seamlessly with built-in collaboration tools, reducing friction and accelerating delivery. - Accelerated Application Delivery
Ship secure applications faster than ever, with confidence that your enterprise is protected against evolving threats.Key
+ Reduced vulnerability remediation time by 70%.
+ Improved collaboration between DevSecOps teams.
+ Faster release cycles with built-in security expertise.
continuous feedback loop for security posture improvement.
The process is fully automated and driven by proprietary Al capabilities. Discover more.
+ Application Zero Trust and Avocado Protect
+ Dev Sec Ops Testing
+ Avocado Reveal for Automation in Application Architecture
+ Automation of Enterprise Application Change management using Avocado Reveal