In today’s hyper-connected digital landscape, application ecosystems are the lifeblood of modern enterprises. These ecosystems are not monolithic; they are sprawling, dynamic, and often span across multi-cloud environments, integrating legacy systems, virtual machines, Kubernetes clusters, and diverse databases. Within these ecosystems, data flows in two primary directions: North-South (N-S) and East-West (E-W). Understanding the ratio and behavior of these traffic types is critical to securing applications and protecting sensitive data.
What is East-West vs North-South Traffic?
- North-South Traffic refers to data that flows between internal systems and external entities, typically between a data center and the internet or external clients. This includes user requests to web applications, API calls from external services, and data exchanges with third-party platforms.
- East-West Traffic, on the other hand, is the internal communication between components within the same data center or cloud environment. This includes microservices talking to each other, database queries, internal APIs, and service mesh communications.

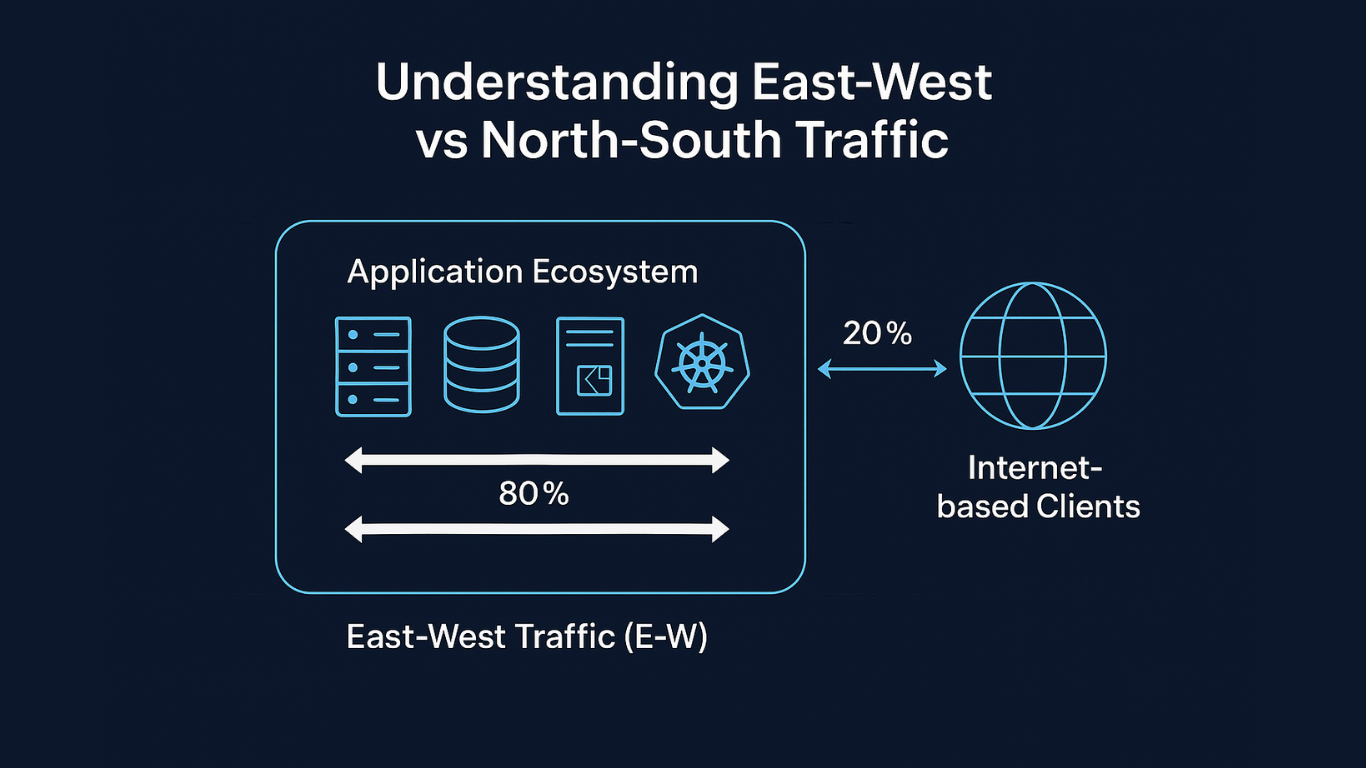
Pic1: Understanding East-West vs North-South Traffic
While N-S traffic is often the focus of traditional perimeter security measures like firewalls and intrusion detection systems, E-W traffic constitutes the majority of data exchanges – approximately 80%, based on research I conducted during my tenure at IBM. This 80:20 E-W:N-S ratio is not just a statistic; it’s a lens through which we must view application behavior and security.
Why the E-W:N-S Ratio Matters
The dominance of E-W traffic has profound implications:
- Security Posture: Traditional security models focus on securing the perimeter. However, once an attacker breaches the perimeter, they can move laterally within the E-W traffic, often undetected.
- Application Behavior: E-W traffic reflects the internal logic and workflows of applications. Monitoring this traffic provides deep insights into how applications function and interact.
- Vulnerability Exposure: With 80% of data exchanges occurring internally, vulnerabilities in microservices, APIs, or databases become prime targets for exploitation.
E-W:N-S Traffic in Key Business Verticals
1. Banking Applications
Modern banking platforms rely heavily on microservices for transaction processing, fraud detection, customer profiling, and compliance checks. These services communicate internally (E-W) far more than they interact with external clients (N-S). For example, a single transaction may trigger multiple internal validations, logging, and risk assessments before a response is sent to the user.
2. Healthcare Applications
Electronic Health Record (EHR) systems, diagnostic tools, and patient portals form a complex web of services. Patient data flows between various internal systems—lab results, imaging, billing, and care coordination—making E-W traffic dominant. Protecting this traffic is crucial to maintaining HIPAA compliance and safeguarding patient privacy.
3. Defense Applications
Defense systems often operate in highly secure, isolated environments. Internal communications between command systems, surveillance modules, and data analytics platforms are extensive. E-W traffic here is not only voluminous but also highly sensitive, requiring robust observability and zero-trust enforcement.
Cybersecurity Implications of E-W Traffic
The complexity and heterogeneity of E-W traffic make it fertile ground for attackers. Once inside the perimeter, threat actors can exploit vulnerabilities in internal services, escalate privileges, and exfiltrate data – all while evading traditional security tools.
Case Study: F5 Networks Breach
A recent malware attack on F5 Networks exemplifies the dangers of unsecured E-W traffic. Attackers bypassed perimeter defenses and infiltrated the development environment, stealing sensitive technology, documents, and source code for products like BIG-IP, F5OS, BIG-IP Next for Kubernetes, BIG-IQ, and APM clients. This breach impacted all F5 clients, prompting emergency product replacements and mitigation efforts. Cybersecurity and Infrastructure Security Agency (CISA) of the United States published in their emergency directive about the details of the malware attack – https://www.cisa.gov/news-events/news/cisa-issues-emergency-directive-address-critical-vulnerabilities-f5-devices
The malware was able to stay within the E-W environment and migrate laterally for about a year. During its operations, it identified sensitive information, source code of products etc. and exfiltrate it to the C&C.
This incident underscores the need for visibility and control within the E-W traffic flows. Perimeter security alone is insufficient.
The Role of Avocado Systems in Securing E-W Traffic
To address these challenges, Avocado Systems offers two powerful solutions:
Avocado Reveal
Provides deep security observability into E-W traffic. It maps application behavior, identifies anomalies, and uncovers hidden vulnerabilities across microservices, containers, and legacy systems.
Avocado Protect
Implements Zero Trust principles within the application ecosystem. It enforces the least privilege access, micro-segmentation, and real-time threat detection, ensuring that even if attackers breach the perimeter, they cannot move laterally.
Together, these tools empower organizations to secure the 80% of traffic that traditional solutions overlook.
Conclusion
The E-W:N-S traffic ratio is more than a metric – it’s a strategic insight into application behavior and security. As attackers evolve, so must our defenses. By embracing security observability and zero trust within E-W traffic flows, organizations can protect their most critical assets and ensure resilience in the face of sophisticated threats.
Ready to secure your East-West traffic? Learn how Avocado Reveal and Avocado Protect can transform your application security strategy. Contact Avocado Systems today at info@avocadosys.com
Avocado Systems is leading the charge in redefining application security for the modern era. It’s time to look inward – because the real threats are already inside.

